Beyond Evasion: Rubrik Zero Labs' Advanced Malware Analysis System Powered By LLMs Exposes Three Novel Threats
Rubrik Zero Labs’ advanced analysis systems identifies rarely seen malware samples belonging to the APT41, GhostPenguin, and Chameleon C2 families.
blog
Beyond Evasion: Rubrik Zero Labs' Advanced Malware Analysis System Powered By LLMs Exposes Three Novel Threats
Rubrik Zero Labs’ advanced analysis systems identifies rarely seen malware samples belonging to the APT41, GhostPenguin, and Chameleon C2 families.
blogOn December 9, 2025, Rubrik Zero Labs’ advanced analysis systems alerted the lab to emerging threats that, to our surprise, were reasonably complex and novel in their mechanisms. After further verification, we identified Linux samples likely belonging to APT41, as well as GhostPenguin malware and an interesting sample named Chameleon C2 that uses WSL functionality within a macro to execute malicious code.

Figure 1: Rubrik Zero Labs LLM-Powered Advanced Analysis Systems
Malware samples
APT41/Winnti Group RAT
Hash: 3752f069d7e54d83f64519f2ad8f9d59224387c50f57f0666b0c5956af40cfb6
VirusTotal Detection: 1 (At time of writing)
First seen: 2025-09-25
Analysis of the extracted code (RZL Advanced Analysis System)
- Malware Family: Likely Winnti (Linux variant) based on code/variable similarity
- Malware Type: Remote Access Trojan (RAT) / Backdoor
Summary
Linux 64-bit RAT/backdoor with comprehensive remote access capabilities including PTY-based shell execution, file transfer, process manipulation, and system reconnaissance. Uses custom RC4 encryption for C2 communications and implements multi-threaded architecture with mutex-based synchronization. Hardcoded connectivity testing to 8.8.8.8 and google.com.
Analysis
The sample is a professionally developed Linux RAT implemented as a 64-bit ELF shared library. The malware demonstrates standard but well-executed RAT capabilities.
Core Functionality
The backdoor provides comprehensive remote control through a custom C2 protocol with RC4 encryption (rc4_crypt_allinone). It implements session-based authentication (auth_request/auth_response) and uses multi-threaded packet handling (recv_thread, sendpkt, recvpkt) with mutex synchronization (resource_mutex).
Remote Access Mechanism
It offers PTY-based shell access through forkPty, which allocates pseudo-terminals using posix_openpt, grantpt, unlockpt, and ptsname. This provides interactive shell sessions with terminal size manipulation (change_term_size, get_term_size) and proper signal handling (sig_child, vhangup).
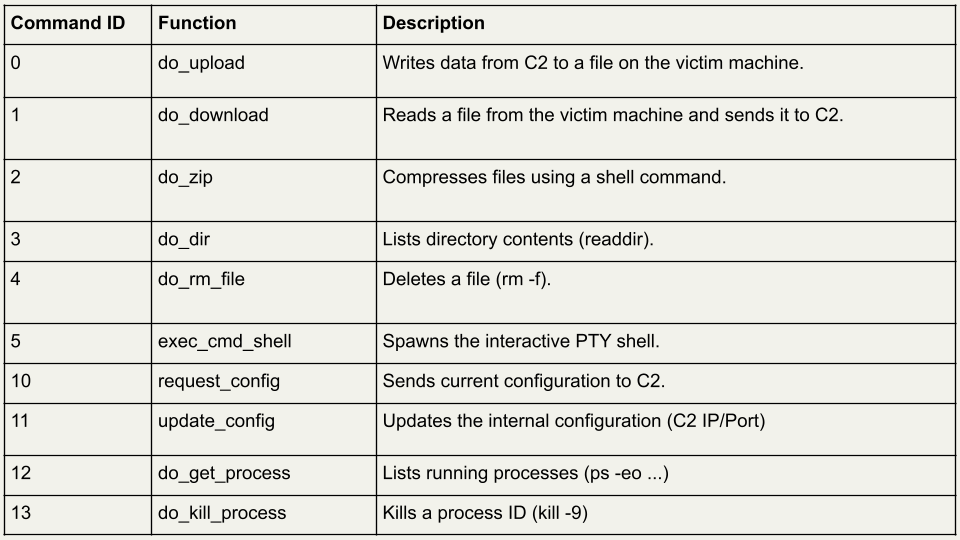
Command Dispatcher (main_proc)
The main_proc function sits in a loop waiting for integer-based commands from the Command & Control (C2) server.
Network Infrastructure
Connectivity testing to hardcoded 8.8.8.8 (Google DNS) and google.com domain suggests infrastructure validation. Custom socket operations (connectex, sendex, recvex, waitex, closeex) wrap standard network functions.
GHOSTPENGUIN RAT
Hash: 7b75ce1d60d3c38d7eb63627e4d3a8c7e6a0f8f65c70d0b0cc4756aab98e9ab7
VirusTotal Detections: 2 (At time of writing)
First Seen: 2025-07-07
Analysis of the extracted code (RZL Advanced Analysis System)
- Malware Family: GHOSTPENGUIN
- Malware Type: Backdoor/RAT
Summary
GHOSTPENGUIN is a custom Linux backdoor using UDP-based C2 with RC5 encryption, providing remote shell, comprehensive file/directory operations, system reconnaissance, and crontab persistence.
Analysis
GHOSTPENGUIN is a Linux backdoor that implements a custom UDP-based command and control protocol with RC5 encryption. The malware demonstrates solid engineering with multi-threaded architecture, packet retransmission/acknowledgment system, and comprehensive remote administration capabilities.
Architecture
The malware uses six main threads—session negotiation, data receiver, self-registration, heartbeat, data sender, and shell output reader. Thread synchronization is managed via pthread mutex.
Cryptography and C2 Protocol
RC5 Encryption: The malware uses the CMyRC5 class to encrypt network traffic. It utilizes the standard RC5 constants (0xb7e15163 and 0x9e3779b9) to generate subkeys.
UDP Beaconing: Unlike many RATs that use TCP or HTTP, this malware relies on UDP (socket(2,2,0)). It initiates a handshake by requesting a Session ID (ThreadProcGetSessionIDFromServer) and then maintains a heartbeat (ThreadProcHeartBeat).
Persistence Mechanism
Cron Jobs: The function ImpPresistence achieves persistence by rewriting the current user's crontab. It constructs a command that ensures the malware (referenced by g_szCurrentProcessName) runs on a schedule, ensuring it survives system reboots.
Remote Shell Implementation
Pipe-based shell: The RShellRun function creates a reverse shell using pipe() and dup2(). It forks a child process, redirects stdin, stdout, and stderr to the pipes, and executes /bin/sh. This allows the C2 server to send shell commands and receive the output in real-time.
Chameleon C2
Hash: 1be5278db096e47426a1efa3283eee25176b8b7ace9133a59dd11a8908326d78, 72e944751fd4c1cd71dfe48a5b6cc3c76a67832381ac59e6be0932c4bc8ac933, c309e08259e0499af154273f71003ea31b048ceaa19e0351db62065ae77279c2
VirusTotal Detections: 26 (At time of writing)
First Seen: 2025-12-08
Analysis of the extracted code (RZL Advanced Analysis System)
Summary
Sophisticated Excel maldoc (VBA macros) that deploys a novel WSL-based Command & Control agent. Checks for Windows Subsystem for Linux availability, then drops a bash script (c2beacon.sh) and PowerShell launcher to establish persistent HTTP-based C2 communication with 192.168.23.51:8443 (malware likely under testing). Features include 30-second beacons, remote command execution, Windows-to-WSL path conversion, and hidden execution via PowerShell.
This analysis represents the first documented malware systematically exploiting WSL as a stealth C2 channel.
Analysis
A custom-developed malicious Excel document containing VBA macros that function as a dropper for a Windows Subsystem for Linux (WSL) based Command & Control agent branded as 'Chameleon C2'. The sample represents a novel approach to malware delivery and persistence by leveraging WSL as an execution environment.
Infection Chain
1. Initial Execution: Multiple auto-execution macro triggers (AutoOpen, Workbook_Open, Auto_Open, Document_Open) ensure code runs when document is opened
2. Environment Detection: auuazonz() function checks if WSL is installed by verifying existence of %SystemRoot%\System32\wsl.exe and testing functionality with 'wsl echo test'
3. Payload Deployment: If WSL is available, gxlpziyl() function deploys the C2 agent
4. Bash Script Creation: Writes c2beacon.sh to temp directory with C2 functionality
5. PowerShell Launcher: Creates wsl_launcher.ps1 to execute the bash script via WSL in hidden window
6. Persistent C2: Bash script runs indefinitely, beaconing every 30 seconds and executing commands
Technical Sophistication
The malware demonstrates several advanced capabilities:
Cross-Platform Architecture: Bridges Windows and Linux environments, using Windows for initial compromise but Linux/WSL for execution and persistence
Path Conversion Logic: Implements intelligent Windows-to-WSL path translation (C:\ to /mnt/c/), enabling seamless file system access across environments
Professional C2 Protocol: Uses JSON-based HTTP POST requests with structured data including agent_id, hostname, username, OS info, timestamps, and command results
Command Execution Framework: Retrieves commands from C2 server, executes via bash, captures output (up to 50KB), and exfiltrates results
Obfuscation Techniques: Heavy use of Chr() concatenation, variable name obfuscation (auuazonz, gxlpziyl, vqmhcjbr), and string building to evade static detection
Anti-Detection: Executes within WSL environment where traditional Windows EDR may have limited visibility
Proper Error Handling: 'On Error Resume Next' throughout to prevent execution failures
Line Ending Conversion: Uses WSL sed command to fix Windows CRLF to Unix LF line endings
C2 Functionality
The dropped bash script implements:
UUID-based agent identification
System information collection (hostname, username, OS)
Persistent beaconing to http://192.168.23.51:8443/api/beacon
Command retrieval via JSON parsing with Python3
Dynamic command execution with output capture
Result exfiltration to /api/result endpoint
Output sanitization (escape sequences, truncation to 50KB)
Evasion Mechanisms
Hidden window execution (-WindowStyle Hidden)
PowerShell execution policy bypass
WSL execution space (potential EDR blind spot)
No suspicious Windows process behavior after initial launch
Bash script appears as legitimate WSL activity
Targeting
Likely targets developer workstations or modern enterprise environments where WSL is commonly installed for legitimate development purposes. The Arabic timestamp in comments suggests possible Middle Eastern development or targeting.
Innovation
It is our understanding that this is the first publicly documented malware systematically exploiting WSL as a C2 execution environment from Office macros. While WSL abuse has been theorized, this represents a practical implementation with production-quality code. The technique exploits the trust boundary between Windows and WSL, where security tools may have reduced visibility into WSL processes.
Conclusion
The landscape of cyber defense is at a critical juncture. As attackers begin to leverage sophisticated AI to launch complex and highly evasive attack scenarios, the advantage appears to be shifting. However, as demonstrated by the discoveries detailed in this report, a powerful counter-response is emerging.
Our advanced analysis system, particularly those augmented by LLM technology, assists in meeting and neutralizing threats at machine speed. The uncovering of the APT41/Winnti Linux RAT with its PTY-based shell, the stealthy, UDP-based GhostPenguin, and the novel Chameleon C2—which systematically exploits Windows Subsystem for Linux (WSL) as a covert C2 channel—showcases the system's efficacy.
These are not simple threats; they are professionally engineered, complex attacks designed to bypass traditional security layers. The ability of our platform to rapidly identify the cross-platform architecture of Chameleon C2 and the custom C2 protocols of the Linux RATs is a direct testament to the power of LLM-driven analysis. This technology allows us to move beyond current practices to analyze code logic and behavioral patterns at scale, ensuring we can operate at machine speed to uncover, dissect, and respond to the most novel threats emerging in the wild.
NEWSLETTER
Get insights straight to your inbox