
For Scattered Spider Victims, Bills Are Still Coming Due
When Clorox filed its lawsuit against IT services giant Cognizant this July, the world was reminded of the eye-popping cost and long slog back to normalcy that a ransomware incident can cause a global brand.
blog
For Scattered Spider Victims, Bills Are Still Coming Due
When Clorox filed its lawsuit against IT services giant Cognizant this July, the world was reminded of the eye-popping cost and long slog back to normalcy that a ransomware incident can cause a global brand.
blog
When Clorox filed its lawsuit against IT services giant Cognizant this July, the world was reminded of the eye-popping sums a ransomware incident can cause a global brand. According to the suit, the incident cost the company $380 million in damages, with $49 million spent on recovery efforts alone.
The complaint detailed the conversation between the cybercriminal and the Cognizant agent they contacted.
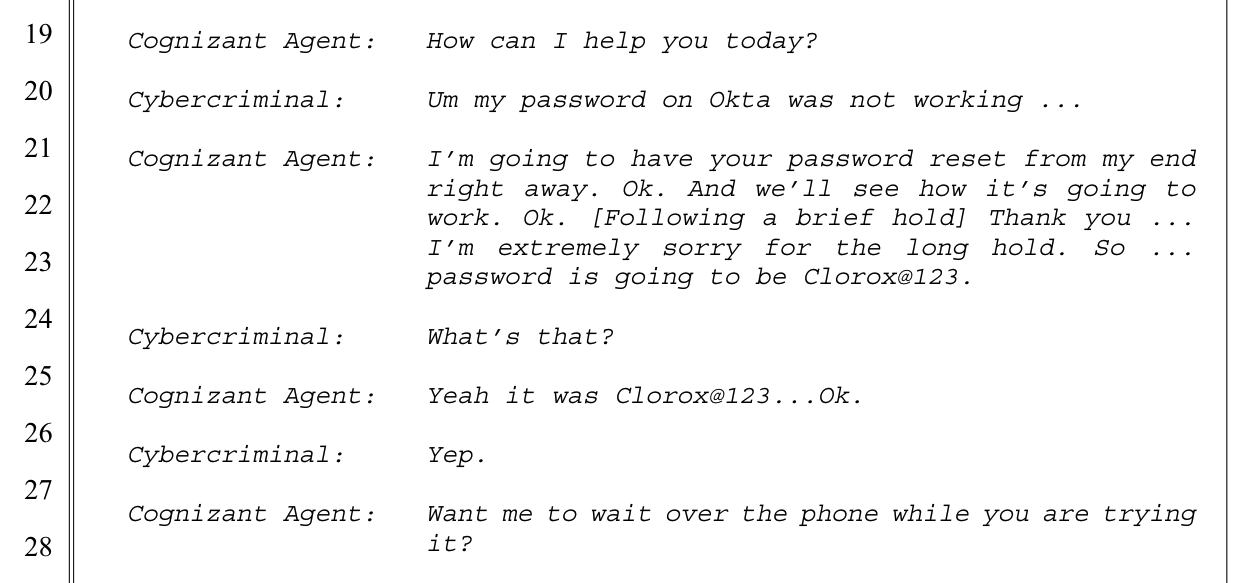
The suspected culprit? Scattered Spider. The tactic? Call and ask for a shiny new set of credentials.
From the complaint:

Lest anyone assume this was an improbable, one-off success from a supply chain scheme gone right, consider that damages from the incident suffered by the retailer Marks & Spencer this spring are likely to exceed $400 million. It follows on similar help desk scams attributed to Scattered Spider and perpetrated against targets, including MGM, Visa, Qantas Airlines, and others.
These incidents drive home not only how financially crippling ransomware attacks can be, but also how extensive the timelines for cleanup can be. Recovery efforts by M&S were ongoing well into late July. Clorox is still seeking damages from an incident that occurred in August, 2023.
The ease with which even strong cyber defenses can be undermined by weaponizing human psychology makes clear that organizations must prioritize resilience and recovery capabilities as strongly as they do initial access prevention or lateral movement detection.
Who is Scattered Spider?
Help desk scams like those described in the Clorox lawsuit have come to define the apparently decentralized, financially motivated threat group known variously as Scattered Spider, Roasted 0ktapus, Scatter Swine, Muddled Libra, and other aliases.
Psychologically savvy and natively English-speaking, the group is known to target help desks and internal IT teams with social engineering tactics playing on basic human traits—empathy, urgency, deference to authority, an urge to act decisively under pressure—to achieve their aims.
But while Scattered Spider may have gotten its start as an initial access broker specializing in social engineering and phishing campaigns, its capabilities have evolved considerably. Once a foothold has been established in the target environment, the group has displayed an impressive knack for lateral movement, with breakout times often measured in minutes rather than hours.
Scattered Spider has also been known to abuse native tools and SaaS services, as well as misconfigurations and bugs in well-known productivity tools, to evade detection and escalate the privileges of compromised accounts. Finally, the group relies on several well-known ransomware-as-a-service (RaaS) brokers including ALPHV/BlackCat, RansomHub, Qilin, and DragonForce for payloads.
Scattered Spider’s evolution as a threat group highlights some essential realities of the cyber threat landscape today. For one, decentralization and loose affiliation limit the effectiveness of law enforcement’s efforts to disrupt their operations. Additionally, Scattered Spider’s ability to consistently adopt new capabilities and tactics speaks to the streamlining and professionalization of cybercrime, where specialist third-parties are regularly subcontracted into what is effectively a supply chain of threat capabilities.
Table 1: Scattered Spider TTPs and Corresponding Defense Strategies
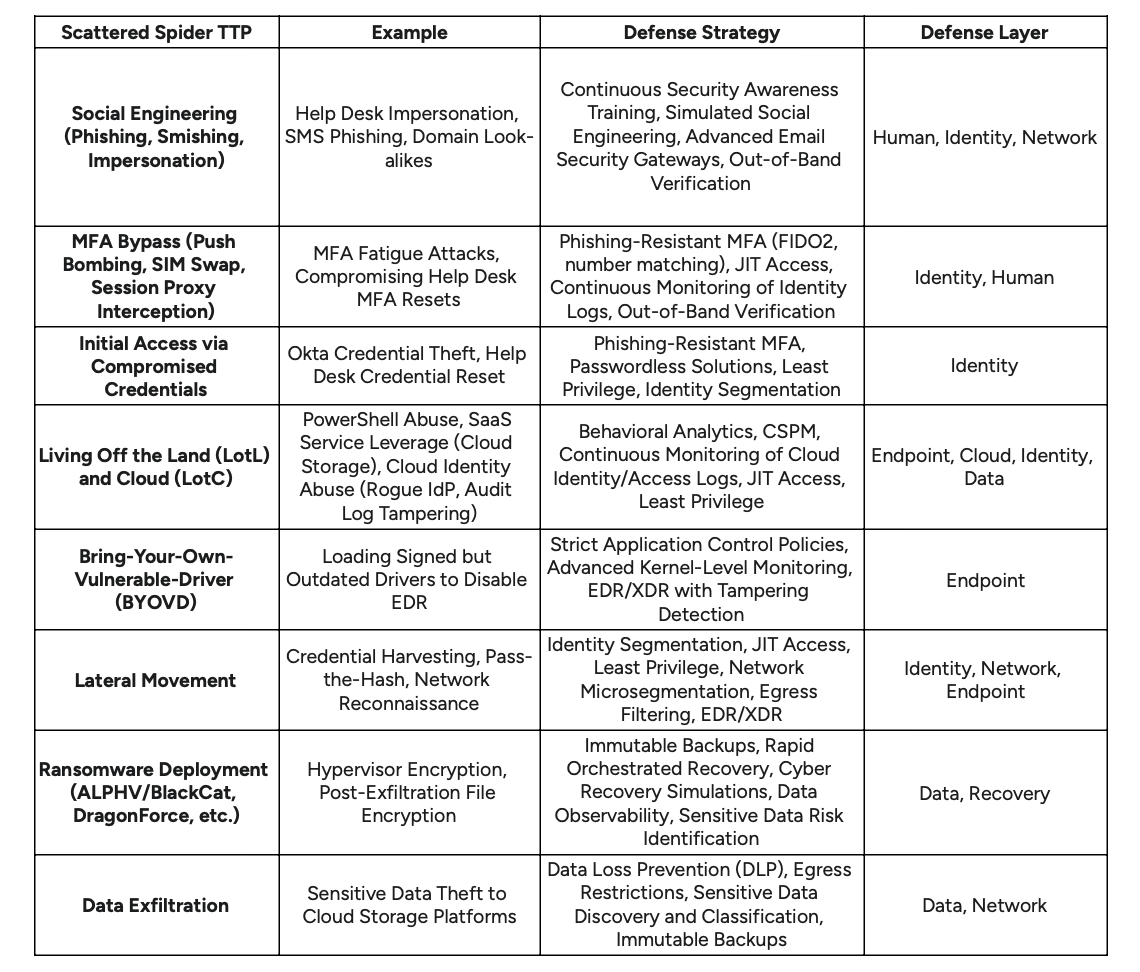
The Weaponization of Identity
While not its sole strength, identity compromise has been the single biggest enabler of Scattered Spider's success. The group understands that compromising even a single high-privilege identity can rapidly lead to a full-scale, enterprise-wide breach, allowing it to bypass numerous technical controls.
The strategy remains the same regardless of the victim: Hack the person and lay low, evading technical controls until maximum leverage is achieved, and then strike with something like a mass encryption event. We’ve seen this play out in recent days based on reports of Scattered Spider targeting ESXi hypervisors to extract Active Directory databases and compromise admin credentials for these resources.
Scattered Spider’s sophistication with cloud-based tools and SaaS applications also hits at another avenue for its evolution. The group has been known to manipulate identity and access management (IAM) policies to escalate privileges, modify policies, or create new cloud instances, casting doubt on the legitimacy of both human and machine-based identities. These compromised identities represent the most direct path to an organization's most critical assets, making them the most vital control point.
Given that the group has experienced such success through social engineering, it’s not unlikely it will double down on what’s worked. This might involve recruiting professional psychologists to help refine its ability to “hack the human” or, more likely, leveraging AI to create ultra-convincing vishing and video deepfake pretexts to fool victims with a fidelity and frequency previously out of reach.
Squashing Spiders: Building Resilience against a Pressing Threat
Countering an adaptive, sophisticated adversary like Scattered Spider requires a multi-layered, zero-trust strategy that addresses not only technical vulnerabilities but also the human element throughout the attack lifecycle. As part of that strategy, there are certain resilience and recovery capabilities that should be prioritized.
IT and technology leaders should hone their focus on:
Protection Against Ransomware and Data Tampering
Ransomware and data extortion form the basis of Scattered Spider’s monetization tactics. Tamper-proof backups ensure data cannot be encrypted, modified, or deleted by external threat actors. This "air-gapping" means backups are logically isolated from the production environment, even if the primary network is compromised. This is critical as Scattered Spider often deploys ransomware or engages in post-exfiltration file encryption. Clean, uncorrupted data copies must always remain available for recovery, regardless of the state of the production systems. Data integrity checks should validate immutability and backup reliability.
Accelerating Detection and Response
Features like anomaly detection can provide early warning of data tampering. By analyzing metadata for changes in file rates, system sizes, and entropy, and detecting VM-level encryption, it can alert security teams to potential ransomware attacks or data tampering attempts. This capability directly contributes to reducing the Mean-Time-To-Recovery (MTTR) by providing early warnings and granular visibility into what data was impacted and how it changed over time, including identifying last-known clean data states.
MTTR is a refined metric for data recovery and ransomware response that goes beyond the traditional “time to restore service.” It breaks down the recovery process into several distinct phases including scoping, restoring, and validating the affected data and applications. By measuring the duration of each of these atomic intervals, a total MTTR can be composed to align with different stakeholder perspectives, like “Security Recovery MTTR” or “Business Service MTTR.” This approach allows organizations to attribute time savings to specific capabilities and provides a more accurate, phase-aware understanding of an organization’s recovery operation performance.
Ensuring Business Continuity and Data Integrity
In the event of a successful attack, rapid recovery capabilities can minimize downtime and data loss, directly impacting the Mean-Time-To-Recovery (MTTR). Teams should prioritize the surgical recovery of impacted applications, files, or objects at scale with simplified workflows. But simply claiming these capabilities isn’t enough. Cyber recovery simulations in isolated environments should be used to test and validate recovery plans, ensuring predictability and reducing uncertainty during an actual incident.
Addressing Identity-Based Attacks
Given Scattered Spider's heavy reliance on identity compromise, rapid and reliable identity restoration capabilities are critical. Organizations must be able to quickly detect, eradicate, and restore Active Directory from a clean, uncompromised baseline in order to combat attackers’ lateral movement and persistence tactics. This is crucial for containing and remediating attacks that exploit compromised credentials.
These techniques are one part in the formula for protecting against attacks like those perpetrated by Scattered Spider. But in light of the group’s ability to circumvent technical controls and the cost and length of recovery efforts, they are worth insisting on.