
Meet the Ransomware Groups Targeting Your Linux-based Cloud Workloads & Backups
The LockBit, Akira, and Clop ransomware families have been known to security researchers for some time. But they continue to be the most prolific threats targeting cloud workloads and backups.
blog
Meet the Ransomware Groups Targeting Your Linux-based Cloud Workloads & Backups
The LockBit, Akira, and Clop ransomware families have been known to security researchers for some time. But they continue to be the most prolific threats targeting cloud workloads and backups.
blogLockBit, Akira, and Clop are ransomware families that have been on the radar of security researchers for some time. Their financial incentives and evolving toolsets that target virtualized ecosystems have made these three groups especially persistent, dominating attacks on Linux-based cloud workloads and VMware vSphere hypervisors. They leverage the high-impact potential of encrypting entire virtual infrastructures to force victims into a precarious position with limited recovery options.
According to data for Rubrik Zero Labs, these three ransomware groups dominate attacks on Linux workloads and vSphere. So it makes good sense to get to know the tactics and technologies of these cybercrime syndicates to help guard against incursion.
In the spirit of “know your enemy” here’s an overview of LockBit, Akira, and Clop—and some recommendations for building resilience against their attacks.
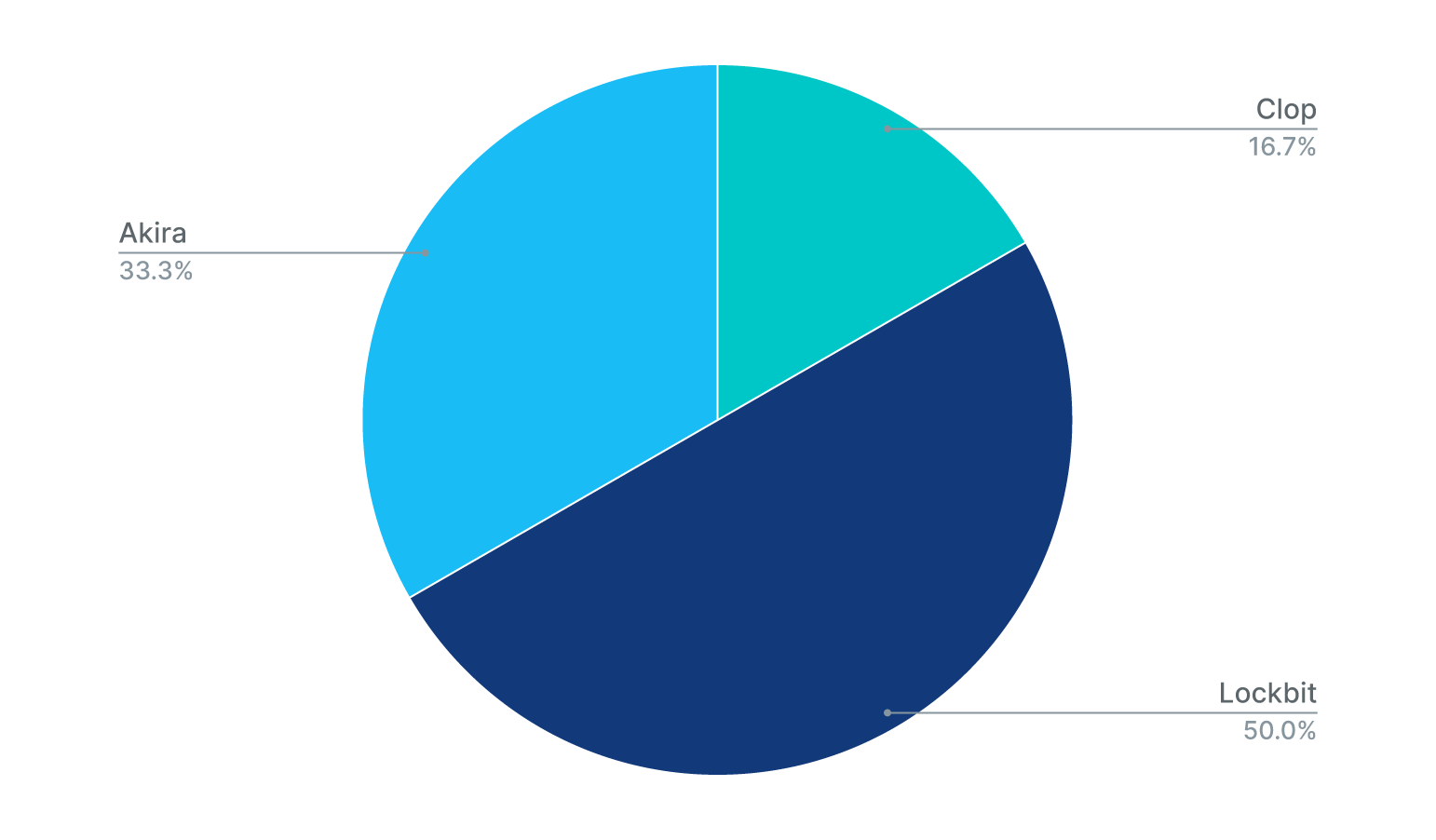
Distribution of LockBit, Akira, and Clop in Rubrik detection telemetry
LockBit Ransomware
LockBit ransomware started by targeting Windows systems, but later expanded its operations to include Linux “encryptors,” with a particular focus on virtualized environments running VMware’s vSphere. LockBit can now compromise both traditional Linux-based servers and VMware hypervisor hosts such as ESXi, which many organizations rely on to manage their virtual machines.
LockBit attackers can encrypt entire clusters of virtual machines simultaneously, maximizing disruption and pressuring victims to pay the ransom. Their tactics involve exploiting weaknesses or misconfigurations in network security perimeters, phishing campaigns, or leveraging compromised credentials to gain access to vSphere infrastructures.
The LockBit operators are very aggressive in ransomware development and have recently released LockBit5.0 with updated capabilities, including the ability to conduct faster encryption. Here are some snapshots of the latest version and its capabilities.
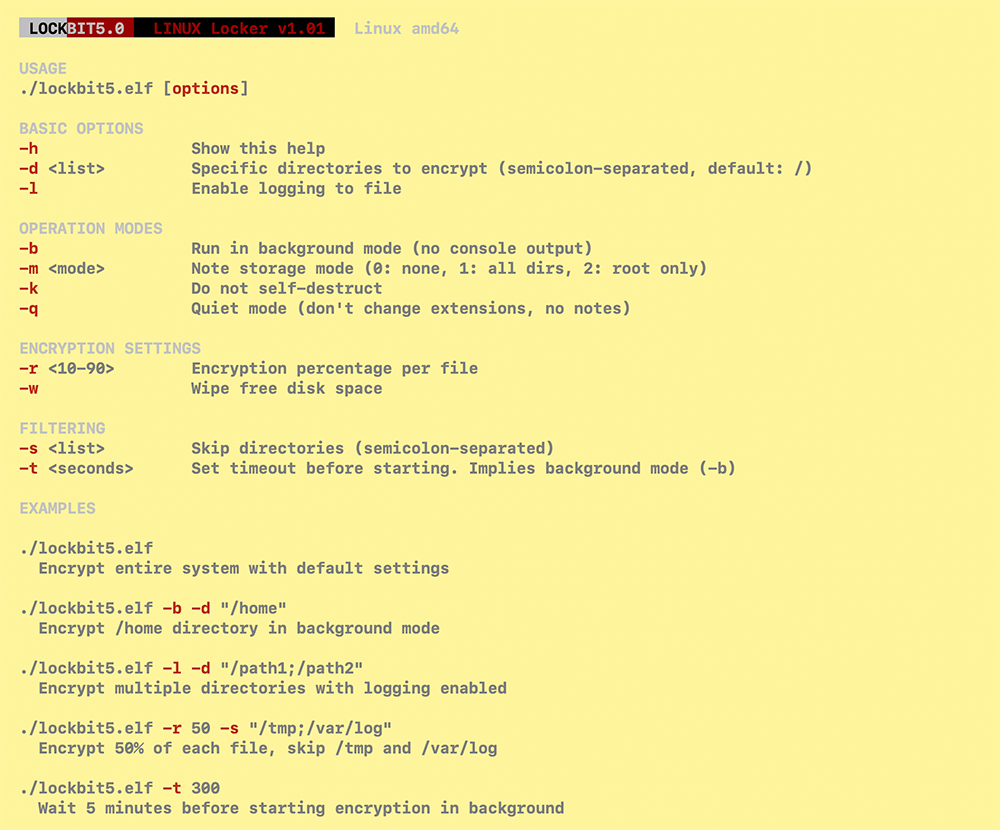
LockBit5.0 Linux variant capabilities
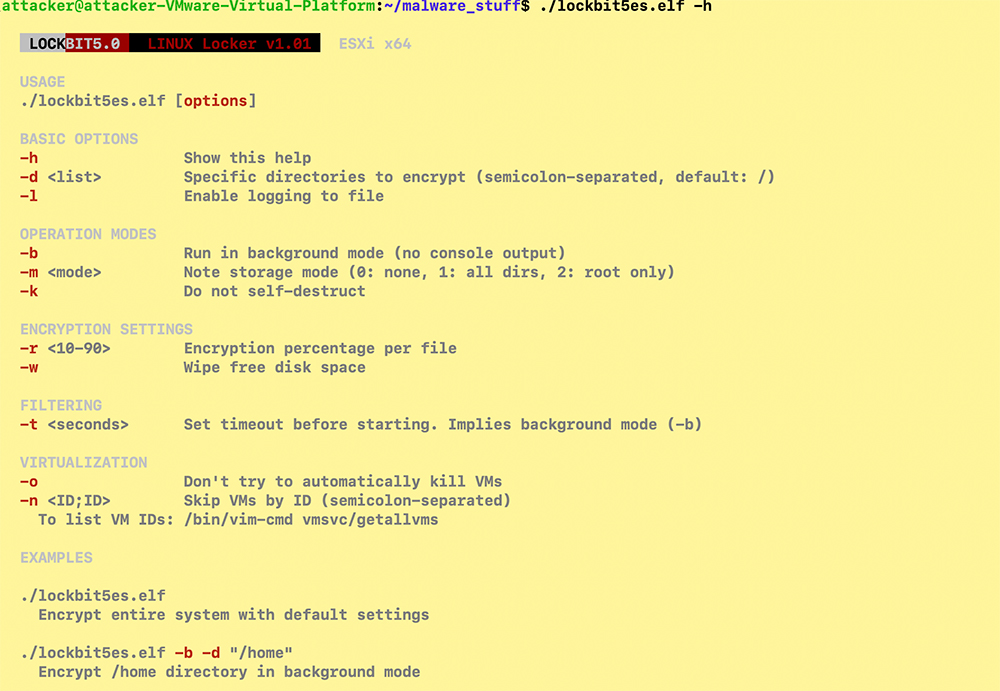
LockBit5.0 ESXI variant capabilities
Akira Ransomware
Akira is another high-profile ransomware group and cross-platform ransomware variant that has joined other ransomware groups in targeting both Linux and VMware vSphere to disrupt virtualized environments.
Akira ransomware targeting Vmware Vsphere
The group employs a partial encryption scheme that accelerates attacks and also relies on double-extortion tactics, threatening to leak stolen data if victims refuse to pay.
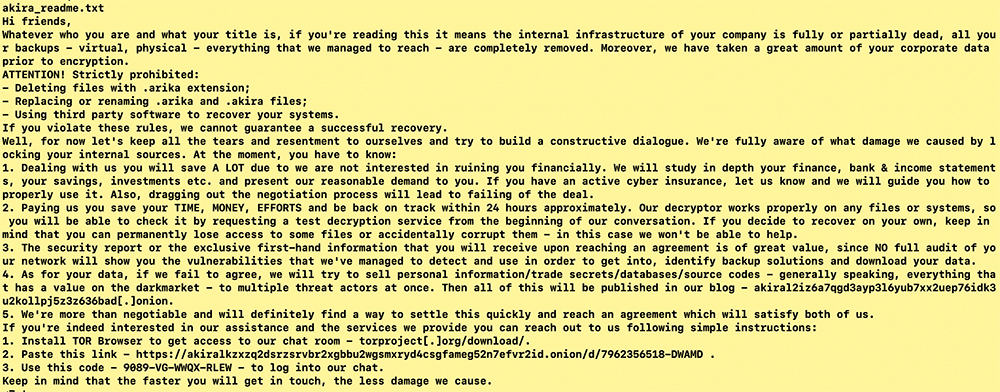
Akira ransom note
This shift toward Linux and vSphere highlights the gang’s expanding reach and demonstrates the growing risks organizations face when protecting their virtual infrastructures.
Clop Ransomware
Clop (Cl0P) is a sophisticated, financially-motivated ransomware group that rose to prominence through large-scale attacks and strategic use of zero-day exploits against enterprise file transfer applications. Clop operators gain privileged access to critical data including sensitive information stored on cloud-connected systems—by targeting vulnerabilities in widely utilized solutions such as Accellion FTA and MOVEit Transfer.
Their motivation lies primarily in extortion, using a dual-threat tactic—data theft followed by encrypted system lockdown—to maximize ransom payments. Clop’s exploitation of unknown or unpatched software flaws highlights their capacity for rapid technical adaptation, as well as a willingness to engage in extensive reconnaissance to identify and capitalize on high-value targets within corporate networks.
In recent days we have seen the spike in Clop ransomware activity in the Rubrik detection telemetry, demonstrating that these actors actively target Linux-based cloud workloads. Although Clop is known for attacking the Windows-based endpoints, its active use on Linux-based workloads expands the risk the group poses to its targets.
Ransomware Resilience Recommendations
Best practices for defending against ransomware in general prove effective against those groups targeting Linux-based cloud workloads and VMware vSphere hypervisors as well.
Among these are:
Data immutability: Immutable file systems mean that once written, data cannot be encrypted or modified—either by malicious actors or human error. This can be achieved through an "append-only" design where new data is written out-of-place, preserving the original. All operations are conducted via authenticated APIs within a zero-trust cluster design, preventing unauthorized access or manipulation.
Zero trust architecture: "Retention locked" backups prevent tampering with SLA policies that may seek to remove protected objects, reduce the specified time for data retention, redirect archival destinations, or delete SLA policies entirely.In other words, "never trust." Quorum authentication requires multiple parties to consent to any SLA changes according to a pre-defined chain of approval—the "always verify" element of backup architecture.
Anomaly detection: AI-driven early detection capabilities leverage machine learning to identify ransomware and other anomalies before they cause widespread damage. Continuous inline scanning of data across on-premises, in the cloud, and across SaaS environments should integrate with threat intelligence feeds to identify potential threats proactively based on metrics like change rates, abnormal system sizes, entropy changes, and VM-level encryption detection. Anomalies should generate alerts via native UI, email, or integration with SOAR/SIEM applications to reduce MTTR by identifying suspicious behavior in backup data.
Orchestrated recovery: Orchestration streamlines policy-driven recovery workflows that define the sequence and dependencies for failover, reducing opportunities for human error and accelerating the recovery process. When orchestration accommodates DR testing procedures, teams can test these workflows frequently to ensure readiness in the event of an incident.
Ransomware families like LockBit, Akira, and Clop will continue their maximum pressure campaigns against victims as long as they remain lucrative. But by employing these best practices before an incident occurs, targets reduce the leverage groups can exert in the event of a compromise and increase their options for recovery.