What's Hiding in Your Backups? Our Analysis Reveals a Major Security Blind Spot
Webshells are malicious scripts commonly designed for remote access and control. Their presence in your backup data may serve as a record of successful defense evasion.
blog
What's Hiding in Your Backups? Our Analysis Reveals a Major Security Blind Spot
Webshells are malicious scripts commonly designed for remote access and control. Their presence in your backup data may serve as a record of successful defense evasion.
blogRubrik Zero labs analyze a massive and unique dataset: detection telemetry from the more than 2.1 million snapshots scanned daily. In conducting our analysis, we’ve unearthed a significant and concerning trend: the persistent presence of webshells. These malicious scripts, often designed for remote access and control, represent a critical vulnerability that can go unnoticed within the seemingly innocuous confines of backup archives. This blog post delves into our findings, highlighting the most prevalent webshells we have discovered and offering insights into their potential impact.
The Silent Infiltrators: What are Webshells?
In essence, a webshell is a malicious script or program uploaded to a web server, often disguised as a legitimate file. Once executed, it grants an attacker remote control over the server, allowing them to execute arbitrary commands, upload/download files, modify data, and even pivot to other systems within the network. The danger of webshells lies in their versatility and their ability to bypass traditional security measures, especially when nested within backup files that are often seen as "safe" repositories.
Discovering webshells within backups is particularly alarming. It indicates that they were at some point present on live systems and, even if remediated, their remnants persist, posing a potential re-infection risk if the backups are ever restored without thorough sanitization.
A Look at the Top Offenders: Webshells Uncovered
Analysis of telemetry from thousands of backup scans revealed a consistent pattern in the types of webshells that frequently appear. Here’s a breakdown of the top contenders by prevalence:
1. P0WNYSHELL: This PHP-based webshell is a well-known tool in an attacker's arsenal due to its user-friendly interface and comprehensive features. P0WNYSHELL provides a wide array of functionalities, including file management, command execution, database interaction, and even network scanning. Its prevalence in backups suggests that it's a go-to choice for attackers looking for a robust and versatile backdoor.
2. CHINACHOP: Known for its stealth and simplicity, CHINACHOP is a compact and efficient webshell often used in targeted attacks. Unlike more feature-rich shells, CHINACHOP focuses on providing core command execution capabilities, making it harder to detect based on file size or complexity. Its small footprint allows it to blend in with legitimate files.
3. PHPSPY: As its name suggests, PHPSPY is a PHP-based webshell designed for information gathering and reconnaissance. It often includes features to retrieve system information, list processes, and access database credentials. Finding PHPSPY in backups highlights the potential for attackers to have successfully extracted sensitive information from compromised systems.
4. ASPXSPY: A potent and full-featured webshell targeting ASP.NET environments, ASPXSPY is a common choice for attackers who have compromised Windows-based IIS servers. It provides a comprehensive graphical interface for file management, uploading, command execution, and database enumeration. Its discovery in our telemetry is a critical finding, highlighting that attackers are actively targeting the full web application stack, not just PHP.
5. 404SHELL: This particular webshell is noteworthy for its deceptive nature. Often masquerading as a legitimate "404 Not Found" error page, 404SHELL attempts to blend into the server's infrastructure, making it harder for administrators to spot. Its presence in backups is a testament to the attacker's ingenuity in camouflaging their illicit activities.
Distribution and Prevalence in Backups
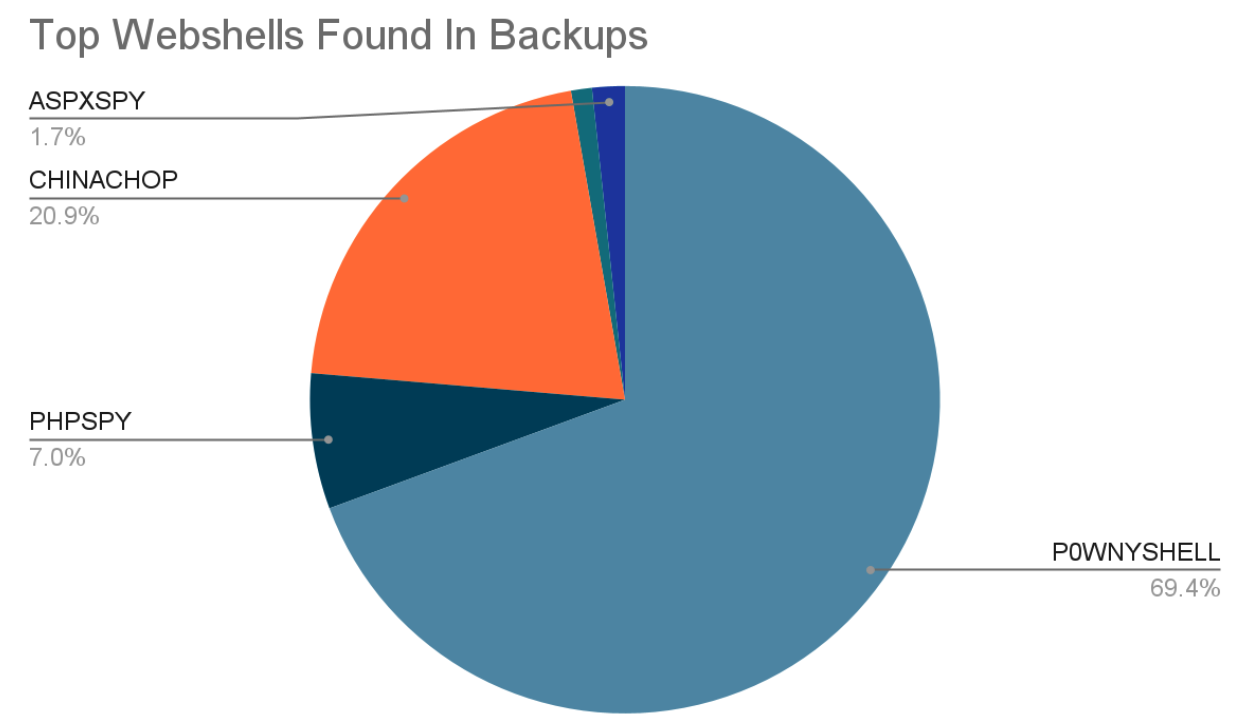
To provide a clearer picture of the landscape, here's a chart illustrating the distribution and prevalence of these webshells detected across the scanned backups.
As the data clearly shows, our backup telemetry is overwhelmingly dominated by P0WNYSHELL, which accounts for over two-thirds of all detections. CHINACHOP follows at a distant second, making up just over 20% of findings. Together, these two "classic" webshells represent 90% of the threats we find lurking in backup snapshots. This suggests that these tools were either extremely successful in historical compromises or are particularly persistent.
Backups vs. The Wild: A Comparative Look
Finding webshells in backups provides a static snapshot of past compromises. But how does this compare to the threats security researchers are seeing actively exploited "in the wild" today? We compared our backup findings against our current threat intelligence data, and the results are striking.
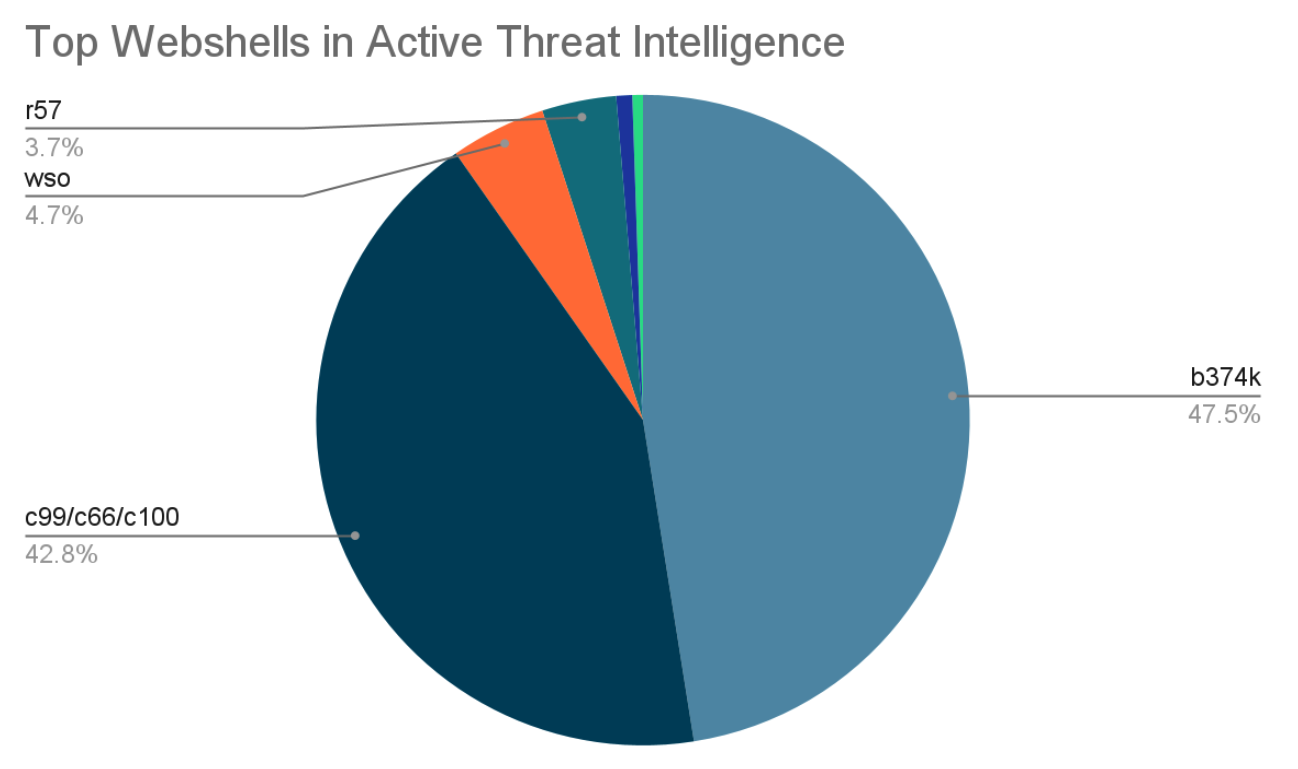
This data paints a completely different picture. The active threat landscape is dominated by newer, more sophisticated shells like b374k (47.5%) and variants of c99 (42.8%).
Clearly, the threats dominating live systems are not the same ones dominating backup archives.
This discrepancy suggests two powerful conclusions.
First, as we've noted, backups are a historical record of compromise. They contain "classic" malware that attackers have used successfully in the past, which live-system monitoring might miss if it's only looking for the "newest" or most popular threats.
Second, and more critically, our data suggests a potential blind spot in live security solutions. The webshells we find so prevalently in backups (like P0WNYSHELL) may be precisely the ones that evaded real-time EDR, WAF, and AV products. If a live scanner fails to detect a threat, that threat persists on the system and is faithfully captured in a backup. It is then detected by Rubrik's comprehensive offline scanning.
This means backup telemetry isn't just a historical record; it's a record of what live security missed.
These threats, having been missed once, pose a clear danger of re-infection should an organization ever restore from one of these compromised snapshots. This highlights the unique and critical value of scanning backups—it provides a dimension of threat intelligence that live-system monitoring alone cannot.
Backup Scanning is a Critical Security Layer
Our analysis of threat telemetry leads to the inescapable conclusion that scanning backups is not simply a "nice to have" or recovery check. It is a critical and necessary layer of an organization's security posture.
The telemetry clearly shows that webshells like P0WNYSHELL and CHINACHOP have successfully evaded real-time security tools in the past (that's precisely how they ended up in the backups). These snapshots, intended for business continuity, become dormant security time bombs, a blind spot for live security products. Restoring from a compromised backup doesn't just recover data; it actively re-infects your environment with a threat that has already proven it can bypass your defenses.
Key Takeaways:
1. Stop Re-infection at the Source: The single greatest risk in a recovery scenario is re-infection. Scanning backups is the only way to sanitize recovery points and ensure you are not re-deploying malware that live systems have already missed.
2. Backups are a Record of Evasion: Our data shows that backup telemetry provides unique intelligence. It's a definitive record of what bypassed your real-time defenses, not just what attackers are trying to do. This makes backup scanning a unique source of truth for security gaps.
3. A Non-Obvious, Critical Defense: The most dangerous threat is the one you don't see. Live monitoring tools focus on the "front door," but attackers are already inside the castle, hiding in your archives. Backup scanning is the essential control that guards this blind spot, ensuring that your last line of defense—your backups—is not your greatest vulnerability.
As security professionals, we must evolve our thinking: backups are no longer just a recovery tool. They are a critical security domain that demands the same level of scrutiny as our live production systems.
NEWSLETTER
Get insights straight to your inbox